The Role of Underground Hacking Groups in the Russo-Ukrainian Cyber War
This post is a part of our ongoing Russia-Ukraine Conflict Series, a series of posts about the less reported aspects of the conflict and its implications for modern cyber warfare. If you are interested in making a donation to help victims in Ukraine, consider this list of organizations.
Introduction
In what has been described as the largest conventional military attack in Europe since World War II, Russian troops invaded Ukraine on February 24, 2022. Less than a week later, this unprecedented military move has already caused the displacement of 2 million Ukrainians and hundreds of deaths on both sides of the conflict. In addition to the shocking political and humanitarian consequences, this ongoing war has had significant implications for information security. As Russian forces launched missiles into Ukraine, they also initiated widespread cyberattacks against Ukrainian digital infrastructure. The dual nature of the Russian attacks demonstrates an important shift in modern warfare, one that is characterized by simultaneous kinetic and cyber attacks.
The cyber aspects of this conflict go beyond the widely-reported malware, distributed denial of service (DDoS), and website defacement attacks. The Russian invasion of Ukraine has sparked involvement at every layer of the cyber world, including underground hacking groups. Within anonymized networks and dark web forums, there has been a significant uptick in hackers engaging in Ukraine- and Russia-related activities. Cybercriminal groups have found ways to profit from the conflict and have even been recruited to aid in both sides of the war.
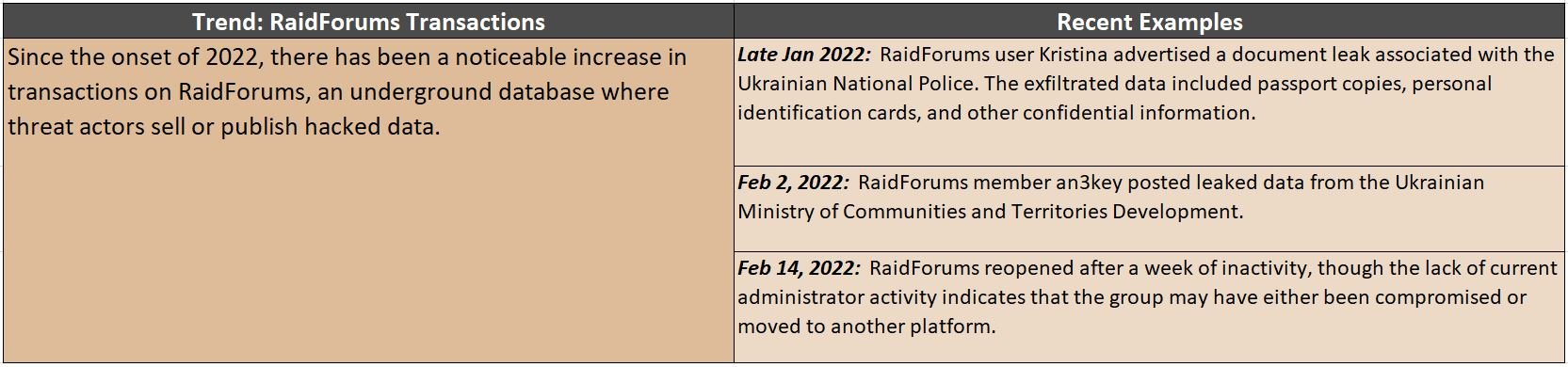
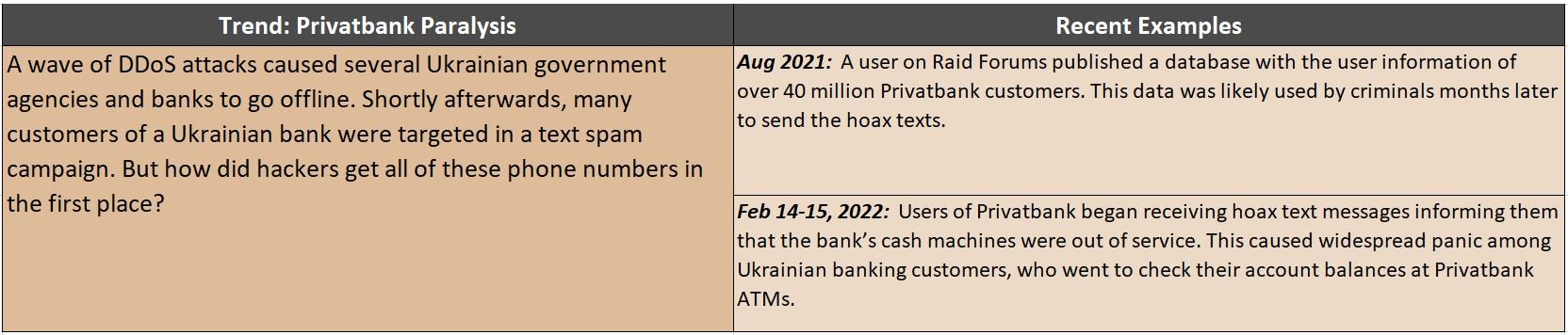
Darknet Profiteering: Leaked Database Sales
First, the money. Cybercriminals have profited from the Russia-Ukraine conflict by selling information on the dark web. Some of the most lucrative resources sold on these underground markets are leaked databases containing personally identifiable information (PII). As Russia was preparing to invade, there was a surge in leaked data related to the Ukrainian government on the darknet. Below are some listed examples of data leaks posted on the darknet in relation to the ongoing war:
(Data source: Recorded Future)
(Data source: DarkOwl)
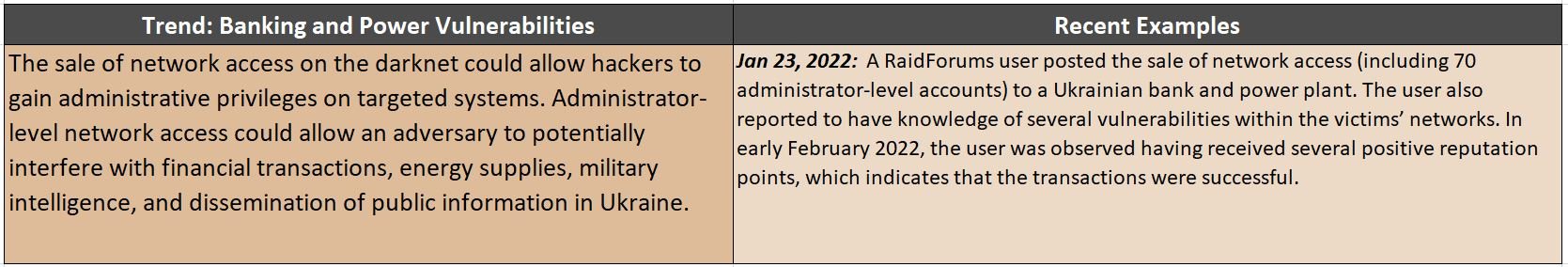
Darknet Profiteering: Network Access Sales
Another valuable data source on darknet marketplaces is network access. In the cyber world, access to confidential information has finite use, but access to a victim’s network has infinite use. Users on the darknet have advertised tools for infiltrating Russian and Ukrainian networks. If acquired, these tools could seriously harm affected organizations and contribute to the intensity of the conflict. Below are some listed examples of network access sales on the darknet:
(Data source: Accenture)
(Data source: Accenture)
In the context of the recent Russian invasion, access to data and networks could significantly enhance the cyber capabilities of both countries. On the offensive side, having network access and the personal details of Ukrainian government officials could allow Russia launch more targeted cyberattacks against Ukraine and lower the morale of Ukrainian troops. On the defensive side, possession of sensitive Russian data or network credentials might allow pro-Ukraine hackers to identify and exploit weaknesses within the Russian forces. Finally, on the neutral side, darknet users with access to this information could simply enrich themselves and begin to exploit other parts of the world.
Recruiting Hackers to Defend Ukraine
Notably, underground hackers are also starting to help defend Ukraine. In fact, the Ukrainian government is actively seeking assistance from covert hacking groups to help defend the country’s critical infrastructure and provide counter-surveillance against Russian troops. Recently, a Ukrainian Defense Ministry official asked Yegor Aushev, the co-founder of Ukrainian cybersecurity firm Cyber Unit Technologies, to help recruit hackers and cybersecurity experts to the Ukrainian cause. Aushev then published a job advertisement reading, “Ukrainian community! It’s time to get involved in the cyber defense of our country.” The post requested that qualified people submit an application with a list of their skills and professional references.
Additionally, some independent hacking groups have launched attacks against Russian infrastructure. Anonymous, a self-identified pro-Ukraine group, claimed on Twitter to have breached Russian government sites and leaked the data online.
Conclusion
Russia versus Ukraine, Ukraine versus hackers, Russia versus hackers, hackers versus hackers - there are many sides to this war. The involvement of cybercriminal groups in the conflict demonstrates an important reality of warfare - that digital networks have evolved to become almost as much of a battleground as physical territory. When leaked data and network access tools end up in the wrong hands, threat actors can cut access to water and utilities, steal government and military data, and cause further chaos.
Want to learn more about the darknet? Check out Phishing for Answers’ post from the #howitworks series during last year’s Cybersecurity Awareness Month: #howitworks: The Dark Web.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-0692. The author's affiliation with The MITRE Corporation is provided for identification purposes only, and is not intended to convey or imply MITRE's concurrence with, or support for, the positions, opinions, or viewpoints expressed by the author.'©2022 The MITRE Corporation. ALL RIGHTS RESERVED.