#latamhackers Series: Week 3 - Reliance on User Execution
This post is a part of our #latamhackers series, a 5-week series about some of the top techniques used by hackers in Central and South America.
#latamhackers Series
During our 5-part series, Phishing for Answers will detail the most utilized hacking techniques in Latin America. Each post will include a summary of the technique, a recent example, and recommended mitigation measures.
Last week, we discussed how regional hackers utilize publicly available toolsets and malware to use against their victims (read more here: #latamhackers: Week 2 - Commodity Tools). This week is all about how these groups rely on the actions of their victims to launch attacks.
Here is the full list of techniques:
Spearphishing
Commodity tools
Reliance on user execution
Geographical targeting
Overseas tool expansion
Week #3: Reliance on User Execution
Summary:
For Latin American APTs, the success of their operations usually hinges on user interaction. In other words, the execution of malicious payloads requires some type of user action – clicking on a link, downloading a file, authenticating to a site, etc. Latin American cyber campaigns do not normally involve zero-click attacks such as Pegasus, a novel Israeli spyware discovered in 2016 that infiltrated iPhones without any end user activity.
Example:
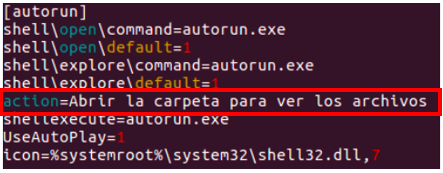
In 2018, many Mexican banking customers began receiving unsolicited texts and emails. In some cases, victims received a digital postcard that read, “Have an excellent day” (in Spanish: ”Te deseo un excelente día). When they opened the messages, the sophisticated malware Dark Tequila was installed onto their devices. Dark Tequila targeted online financial information and login credentials of well-known websites, such as public code repositories and cloud storage accounts. This malware depended entirely upon user interaction in order to deploy its malicious payload, leveraging spearphishing and infected USB devices to reach its objectives.
Code snippet from Dark Tequila prompting users to “Open folder to see files.” (Source: Kaspersky SecureList)
Mitigation measures:
Aside from exercising vigilance when opening messages from unknown senders, users should only utilize removable drives purchased from reputable sources. An even more resilient approach would be to block all USB ports. On a related note, organizations should deactivate the immediate execution option on all systems, which would allow computers to automatically open memory data once connected to a USB drive. Additionally, email programs should be equipped with reliable antimalware/antivirus solutions, cookies should be disabled on web browsers and online financial applications should employ multi-factor authentication (MFA).
Coming Up Next Week – What Will Technique #4 Be?
Next week, the #latamhackers series continues with a discussion of the next technique – geographical targeting. This post is all about the strategies used by Latin American cybercriminals to exploit victims based on their location.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-02304-3.©2022 The MITRE Corporation. ALL RIGHTS RESERVED.